As people become more aware of how malware works, malware developers have had to up their game in order to trick people into downloading their payloads. One of the most interesting methods to appear in recent days is a type of malware that starts by modifying the way a shortcut on the desktop works so that it executes a file. This is a very interesting attack vector that people should definitely watch out for in the future!
ContentsHow desktop shortcuts workHow the attack worksHow to stop itRemove malicious shortcuts
This particular attack strain begins life as a Word macro. Somehow you will have downloaded a document in Russian with a photo of a house on it, but theoretically this macro could be inserted into any document.
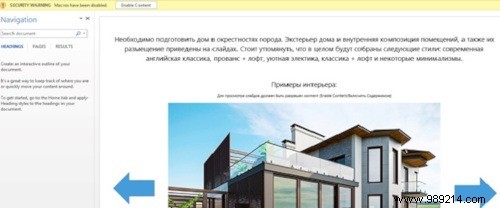
Image of Tendance Micro's infected document.
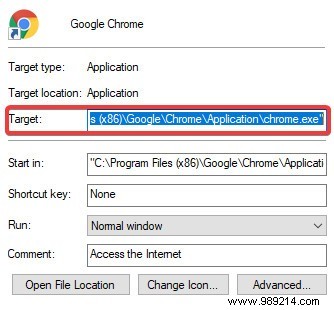
Once the macro is activated, the malware looks for specific shortcuts on the desktop. This includes Chrome, Firefox, Internet Explorer, Opera and Skype. Once it finds one, it downloads a malicious executable file, then changes the target of the shortcut it found to point to the malicious file.
When the user double-clicks on the infected shortcut, it ends up executing the infected target and more malicious code is downloaded. Part of the code includes setting up an Ammyy administrator, remote desktop software that malware developers maliciously use to take control of people's computers. It also collects some system information and emails it to the attacker.
Of course, constantly checking your desktop shortcuts for modified targets isn't ideal! The best defense here is not to download shady documents, let alone run macros from them. Always check that the document you are downloading comes from a good source.
Of course, this may be the start of something bigger as people tackle this new attack vector. In this case, a powerful antivirus should hopefully detect malicious executables being installed and warn you about them before they can do any damage. There are plenty of free antiviruses available that do an amazing job of protecting your PC despite their non-existent price.
The prospect of your desktop shortcuts suddenly turning into malware activators can be a pain, but getting the malware onto your system in the first place involves many steps that should never be performed in general. Now you know how to dodge this attack and can be aware of it in the future if it comes back.
What do you think of this malware attack vector? Does this worry you? Let us know below.
Image credit:Office - front