Hackers have a trick up their sleeve to bypass security suites. Antiviruses rely on "signatures" to detect whether a program is malicious or not. When a new virus is detected, its signature is recorded and sent to everyone else's antivirus software to help them detect it. In a way, the signature is the fingerprint of the virus on a criminal record; once it has been "caught", everyone is notified to evict this malware as soon as it appears.
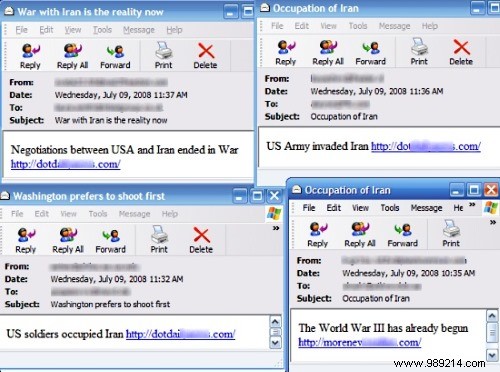
The Storm Worm is an example of polymorphic malware in the wild. He arrived on the scene in 2007 and got his name because his original attack method sent an email with the subject "230 dead as storm hits Europe". Once the victim was infected, their computer would then generate a new strain of the malware every thirty minutes and send it out. The subject line would change over time (as seen above), but the core worm code remained the same.
Metamorphic malware is much meaner. While polymorphic has a telltale core that can be detected, metamorphic malware tries to rearrange its entire code with each iteration. It brings together the same logic and functionality as before, but adds things like mock code and revamped functions to make it different from its previous generations. This makes it much harder to nail and detect.
As we head into a world of increasingly better AI, a fight between malware developers and security programmers is underway. Both sides are using AI to improve their side of their fight to gain an edge over their competition.

With AI leading polymorphic and metamorphic malware, code restructuring is quick and efficient. This means harder-to-detect malware that spreads further and evades more antivirus.
Of course, with security companies also having access to high-end AI, the fight goes both ways. Antivirus developers can program on-the-fly detection that does not depend on signature detection. Using AI that makes logical decisions about how malware acts, it doesn't have to rely on fingerprints – it just needs to spot the agent in action and quarantine it.
It can be a little scary to hear about malware dodging security, but that doesn't change the fact that the best antivirus is your own common sense! Don't download shady files, open suspicious emails, or click on weird links your friends on social media send you. Metamorphic malware can't attack you if you never give them the chance!
With antivirus prevalent on the internet, malware developers need to up their game to circumvent security. Now you know about morphing malware and the threats it poses.
Do you think the morphing code will get worse? Or will security companies win the AI war? Let us know below.
Image source:Cybercrime Wikifoto