Don't let the name "Pretty Good Privacy" mislead you. PGP encryption is the gold standard for encrypted communication and has been used by everyone from nuclear activists to criminals since its invention in 1991. Although the execution is complex, the concept is simple:having the key to the decode.
ContentsHow does it work?What can I use PGP encryption for?How do I get started?ConcludeImagine you want to send a letter to someone but no one but the recipient can read it. The best way to do this is to write the letter in code, but you can't send the code key with the letter, because it's not very secure.
PGP encryption gets around this problem by using public key encryption. Everyone is assigned two keys:a public one that you can share with everyone and a private one that you keep to yourself. What makes this system possible is that the codes only work one way. If key A encrypts a file, key A cannot reverse the process and decrypt it. Only his pair, Key B, can do that. Here's how it usually works:
1. Write your message.
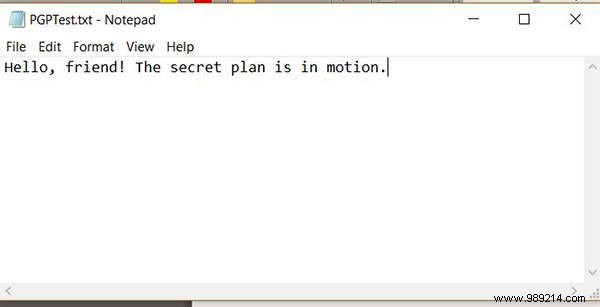
3. Run a computer program that uses the public key to convert the message into code.
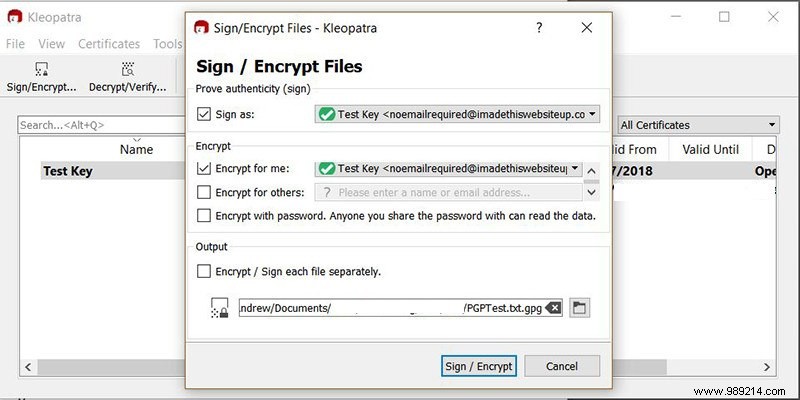
4. Send the message. Anyone who intercepts it will only see gibberish.
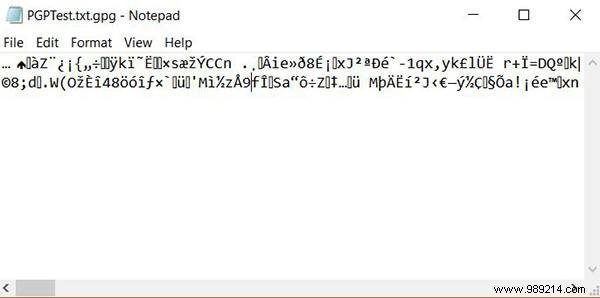
5. Your friend receives the message and runs it through their private key to decode it, restoring it to plain text.

This is a greatly simplified explanation of the process, but anyone curious about nuts and bolts can find many more technical resources online.
PGP is most commonly used to encrypt email, and there are plenty of services to help you do this, such as Thunderbird's Enigmail add-on. Beyond that, you can use your imagination:PGP can encrypt any text you need and can even be used on entire directories and drives. Investigative journalists often list their public keys online to make it easier for anonymous sources to contact them, and sellers on darknet markets often use it to ensure their clients' personal information remains secrets.
Getting your own key pair is actually a lot easier than it looks. You don't need to understand anything about cryptography. You just have to learn some simple programs.
1. Download Gpg4win. This is a free (although you can donate) set of encryption packages and tools. For Mac, see GPG Suite. You can also add it to Linux. As I am using Windows, I will follow the Windows process.
2. Install Gpg4win. Make sure you have GnuPG (the actual encryption package) and Kleopatra (a nice user interface) installed. The other components are optional, but it can't hurt to have them.

3. Once everything is installed, find the Kleopatra program on your computer and open it.

4. Go to the "File" tab and select "New Certificate".

5. Since you want PGP keys, select "Create personal OpenPGP key pair".
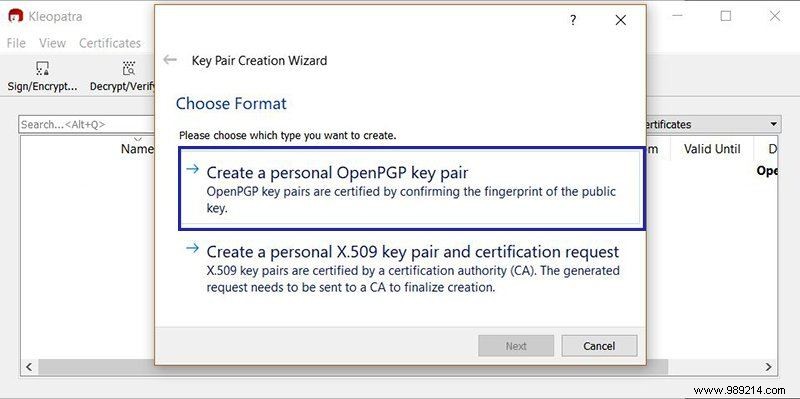
6. If you want to associate your key with your identity, real or fake, you can enter that information here. Otherwise, you can skip this step.

7. Visit "Advanced Settings" and make sure "RSA" is selected. Change the default 2048 to 4096; this level of encryption makes your encryption virtually impenetrable and doesn't really slow you down during normal use.
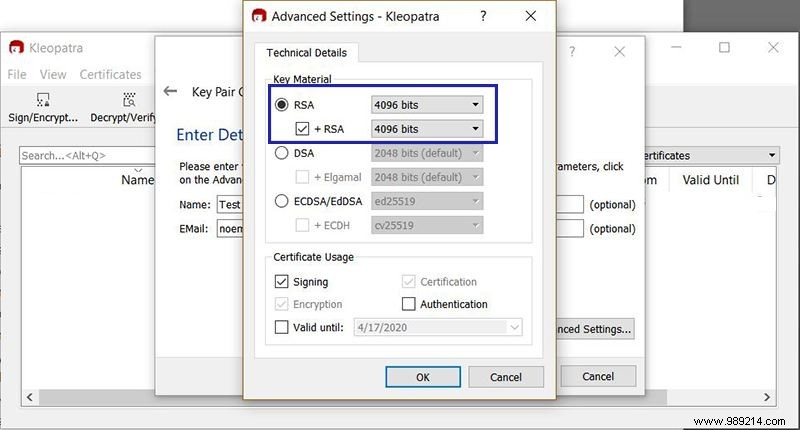
8. Click "OK" to exit this settings menu, then click "Next" to begin creating your key. The program now generates thousands of random characters to create your keys and will ask you for a passphrase. It's unrecoverable, so don't forget it! You can use a password manager if you want.

9. You now have a public and private key! If you want, you can save them in a separate file somewhere, or you can email/publicly upload your public key.

10. You can generate a file containing your public key by right clicking on the file and clicking "Export". There are several ways to see this, but this makes it easy to access your public key whenever you want, without needing to use Kleopatra.

11. Choose where to save the file (it will be saved as an ASCII .asc file), then open any text editing application, such as Notepad.
12. Go to "File", then "Open", set your file type to "All Files" and find the public key file you saved it in.
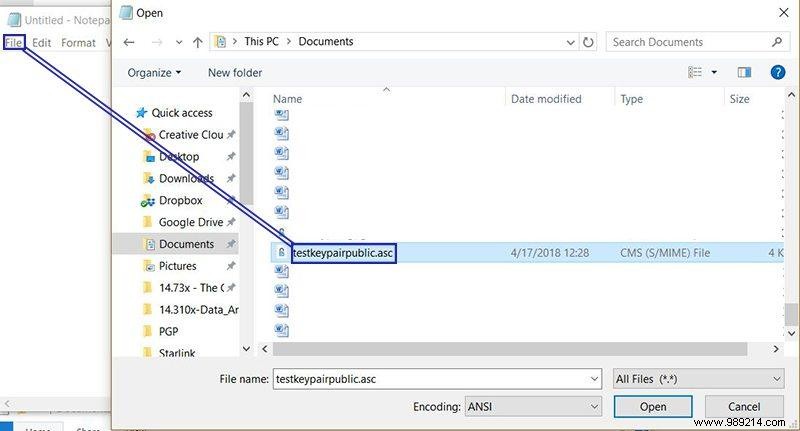
13. Open it with your text editor to see your public key! Beautiful, isn't it?

14. You can export your private key by following the same process except selecting "Export Secret Keys" instead of just "Export". Be sure to store it in a safe place or just keep it inside Kleopatra; it is perfectly accessible there.
These public and private keys can be used with any program that works with PGP, and Kleopatra itself can encrypt and decrypt files using your keys. If you want to test them, try encrypting a text file with your public key and decrypting it with your private key.
PGP encryption is only secure as long as your private key remains private. If someone gets their hands on it, they will be able to read anything encrypted with your public key. Depending on how secure you want it to be, you can keep your key on your hard drive, perhaps behind a few extra layers of security, or you can put it on some more or less secure form of removable storage, like a thumb drive. encrypted. A fingerprint USB flash drive also works well, such as the Lexar JumpDrive Fingerprint F35 USB 3.0 Flash Drive.